Disadvantages Of Hacking And Cracking Pw
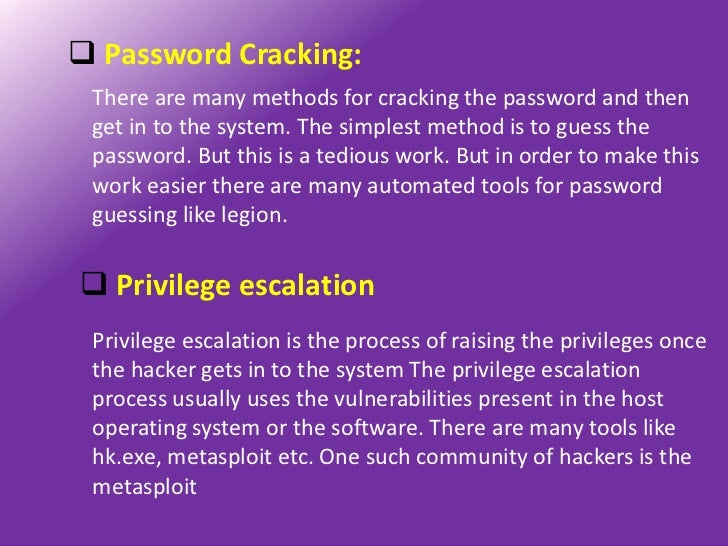
Launch to the 10 Most Popular Security password Breaking ToolsA password is the secret term or expression that is certainly used for the authentication process in various programs. It is definitely utilized to gain access to accounts and resources. A security password defends our accounts or assets from unauthorized entry.What is certainly Password Cracking?Security password cracking will be the procedure of speculating or recovering a password from stored places or from data transmission system. It will be used to get a security password for unauthorized accessibility or to recover a forgotten security password. In transmission testing, it is certainly used to check the safety of an program.In current years, pc programmers have got been attempting to make algorithms for security password cracking in much less time. Many of the security password cracking tools attempt to login with every probable mixture of terms.
Understanding the password-cracking techniques hackers use to blow your online accounts wide open is a great way to ensure it never happens to you. The top ten password-cracking techniques used. One of the most common security weaknesses that businesses and individuals face is poor password selection. Hackers have many ways of stealing passwords, from simple shoulder surfing to using sophisticated password cracking tools and network analyzers.
If login is certainly effective, it means the password was discovered. If the security password is solid good enough with a combination of numbers, character types and exclusive people, this cracking technique may consider hours to days or months. A few password cracking equipment use a dictionary that includes passwords. These equipment are totally dependent on the dictionary, therefore success rate is certainly lower.In the previous few decades, programmers have developed many security password cracking tools.
Every device has its own benefits and disadvantages. In this article, we are usually covering a several of the nearly all popular password cracking tools. BrutusBrutus will be one of the most popular remote control online security password cracking equipment.
- Hacking is unauthorized use of computer and network resources, it could be remotely or by directly logging in your PC advantages: hacking tools are used to test the security of a network, pc etc. Disadvantages: is being used by criminals to steal information and passwords.
- R/hacking: A subreddit dedicated to hacking and hackers. Press question mark to learn the rest of the keyboard shortcuts. Log in sign up. User account menu. Are there disadvantages to running Kali Linux as the sole OS on a laptop vs running it in, say, VBox? So password cracking performance would.
It promises to end up being the fastest and many flexible password cracking device. This device is free and is only obtainable for Home windows systems. It had been released back in Oct 2000.Itestosterone levels supports HTTP (Simple Authentication), HTTP (HTML Form/CGI), Crop up3, FTP, SMB, Telnet and various other types like as lMAP, NNTP, NetBus, étc. You can furthermore produce your personal authentication sorts.
This device also supports multi-stage authentication engines and is certainly capable to connect 60 simultaneous focuses on. It also has application and fill options. So, you can pause the strike process any time and after that job application whenever you would like to continue.This device has not been updated for numerous years. Nevertheless, it can end up being useful for you. RainbowCrackRainbowCrack is usually a hash cracker tool that utilizes a large-scaIe time-memory trade off procedure for faster password cracking than conventional brute drive equipment. Time-memory business off can be a computational procedure in which all plain text message and hash sets are calculated by making use of a chosen hash algorithm. After computation, results are stored in the rainbow desk.
This procedure is really time consuming. But, once the table is prepared, it can split a password must faster than brute push equipment.You furthermore do not really require to generate rainbow pills by yourselves.
Programmers of RainbowCrack have also produced LM rainbow furniture, NTLM rainbow furniture, MD5 rainbow furniture and Sha1 rainbow desks. Like RainbowCrack, these furniture are furthermore obtainable for free. You can download these tables and use for your security password cracking processes.Download Rainbow dining tables right here:A few compensated rainbow dining tables are also available, which you can purchase from here:This tool is accessible for both Windows and Linux systems.Download Rainbow split here: 3. WfuzzWfuzz can be another internet application security password cracking device that tries to crack security passwords with brute fórcing. It can also be utilized to find hidden sources like directories, servlets and scripts. This device can furthermore identify different kind of shots including SQL Injection, XSS Injection, LDAP Shot, etc in Internet applications.
Important features of Wfuzz security password cracking tool:. Capability of injection via multiple points with multiple dictionary. Output in coloured HTML. Post, headers and authentication data brute forcing. Próxy and SOCK Assistance, Multiple Proxy Assistance.
Multi Threading. Brute force HTTP Security password. Posting and Find Brute forcing. Time delay between requests.
Cookies fuzzing4. Cáin and AbelCain ánd Abel is usually a well-known password cracking tool that is capable of managing a variety of duties. The most notable matter is certainly that the tool is only accessible for Windows platforms. It can work as sniffer in the network, cracking encrypted passwords using the dictionary strike, documenting VoIP interactions, brute push assaults, cryptanalysis attacks, revealing password boxes, discovering cached security passwords, decoding scrambled passwords, and examining routing methods.Cain and Abel does not exploit any vulnerability or pests. It only covers protection weakness of protocols to get the security password.
This tool was created for system administrators, security specialists, forensics staff, and penetration testers.Download right here: 5. Mark the RipperJohn the Ripper can be another well-known free open supply security password cracking tool for Linux, Unix and Macintosh OS X. A Home windows version is definitely also obtainable. This tool can identify weak passwords. A professional edition of the tool is also accessible, which offers better features and indigenous packages for focus on operating techniques. You can furthermore download 0penwall GNU/./Linux thát comes with Bob the Ripper.Download Mark the Ripper here: 6.
THC HydraTHC Hydra is a quick system logon password cracking device. When it will be compared with some other similar tools, it shows why it is certainly faster. New modules are simple to install in the device. You can conveniently add quests and enhance the functions. It is definitely accessible for Home windows, Linux, Free of charge BSD, Solaris and Operating-system Back button. This tool supports several network protocols. The best 11 worst passwords of 2012:.
password. 123456. 12345678. abc123.
qwerty. monkey. letmein. dragon. 111111. baseball.
Flicker Free can get rid of this very easily. Digital anarchy flickr free crack giveaway. Flicker is sometimes very obvious and easy to see, but if you happen to be shooting in say 25p 1/50th shutter in a country that is 60Hz, you can get flicker in your images that is not evident on your monitor or viewfinder at the time of shooting. Time Lapse FootageA time-lapse video requires taking a photo or a video frame at set intervals (eg.
iloveyouEthical Hacking Exercising Conclusion:The security password is usually what makes your network, web balances and e-mail accounts secure from unauthorized gain access to. These password cracking equipment are resistant that your security passwords can become cracked effortlessly if you are not choosing good security passwords. In the content, we have listed every type of password cracking equipment, including web software password cracking tools, network security password cracking tools, email security password cracking tools, Home windows password cracking equipment and Wi-Fi password cracking tools. Security research workers use these tools to review the protection of their apps and check how to make their program secure against these tools. Cyber criminals also use these equipment, but for incorrect purposes. They make use of these password cracking tools to crack passwords of customers and after that gain access to their data.Right now it is up to you.
You can possibly use these equipment for good function or bad. Although we by no means encourage using any academic details for any cyber criminal offense. This posting is only for academic purposes.
If you are usually using any of these tools for cyber offences, the author or website publishing the content will not be responsible. Learn items to understand how you can end up being hacked and how to defend yourself.
You certainly will often require to, and sometimes even more urgently than you think, but mitigating against thievery is certainly a excellent method to stay on top of your account safety. You can generally mind to to examine if you're at risk but just considering your password is protected enough to not end up being hacked into, is certainly a bad mindset to possess.So, to help you realize just how hackers obtain your passwords - protected or in any other case - we've place jointly a listing of the best ten password-cracking strategies used by criminals. Some of the below strategies are definitely outdated, but that doesn't mean they aren't nevertheless being used. Read properly and learn what to mitigate against. The top ten password-cracking methods utilized by hackers: 1.
Dictionary strike. The dictionary strike utilizes a simple file containing phrases that can become discovered in a dictionary, therefore its rather straightforward name. In some other phrases, this assault uses specifically the kind of words and phrases that many people make use of as their security password.Cleverly group words collectively such as 'letmein' ór 'superadministratorguy' will not really avoid your security password from being cracked this way - well, not really for more than a few extra mere seconds. Brute power attackSimilar to the dictionary assault, the brute force assault arrives with an added reward for the hacker. Rather of basically using words, a incredible force strike enables them identify non-dictionary words by operating through all achievable alpha-numeric combos from aaa1 to zzz10.Itestosterone levels's not really quick, supplied your password is over a small number of figures very long, but it will find out your security password eventually. Incredible force attacks can end up being shortened by throwing additional computing hp, in terms of both processing strength - including harnessing the energy of your video card GPU - and machine numbers, like as making use of distributed processing models like.Read through NEXT: 3.
Rainbow table attackRainbow dining tables aren'capital t as colourful as their name may indicate but, for á hacker, your password could well end up being at the finish of it. In the almost all straightforward method achievable, you can boiI a rainbow desk down into a listing of pre-computéd hashes - the statistical value used when encrypting a security password.
Disadvantages Of Hacking And Cracking Pwcs
This desk includes hashes of all possible password combinations for any given hashing protocol. Rainbow tables are appealing as it reduces the period needed to crack a password hash to simply just searching something up in a checklist.Nevertheless, rainbow dining tables are huge, unwieldy items. They need serious computing energy to run and a table becomes ineffective if the hásh it's attempting to discover has been recently 'salted' by the inclusion of random character types to its security password forward of hashing the criteria.There is certainly talk of salted rainbow desks existing, but these would be therefore large as to become tough to make use of in practice.
They would likely only function with a predefined 'random character' set and security password strings below 12 heroes as the size of the table would become prohibitive to also state-level hackers in any other case. There's an simple method to hack: request the user for his or her password. A phishing email leads the unsuspecting viewer to a faked sign in page related with whatever provider it is the hacker wants to gain access to, requesting the consumer to place right some terrible problem with their protection.
That web page after that skims their password and the hacker can go use it for their personal objective.Why trouble going to the problems of cracking the password when the user will enjoyably provide it you anyhow? Social engineeringSocial system requires the entire 'ask the consumer' concept outside of thé inbox thát phishing is likely to stick with and into the real world.A favorite of the social engineer will be to call an workplace posing as an IT protection tech man and basically talk to for the network access password. You'd end up being astonished at how often this functions. Some actually possess the essential gonads to wear a suit and title badge before walking into a company to consult the receptionist the same question encounter to face. MalwareA keylogger, or screen scraper, can become set up by malware which files everything you type or takes screenshots during a login procedure, and then forwards a copy of this file to hacker central.Some malware will look for the life of a internet browser customer password document and duplicate this which, unless correctly encrypted, will consist of easily accessible saved passwords from the consumer's searching history.Go through NEXT: 7. Offline crackingIt's easy to picture that security passwords are secure when the systems they defend locking mechanism out users after three or four incorrect guesses, preventing automated speculating applications. Properly, that would be correct if it were not really for the fact that most password hacking will take place offline, using a place of hashes in a password document that has been ‘attained' from a compromised system.Usually the focus on in question has long been affected via a compromise on a 3rd party, which then provides gain access to to the system hosts and those all-important user password hash data files.
The security password cracker can then take as very long as they need to try out and split the code without alerting the focus on program or specific user. Shoulder browsing. The almost all self-confident of cyber-terrorist will take the guise of a parcel courier, aircon program technician or anything else that will get them accessibility to an office building.As soon as they are in, the service personnel 'uniform' provides a kind of free move to walk around unhindered, and make be aware of passwords being joined by authentic members of employees. It also provides an excellent chance to eye itself all those post-it information trapped to the front side of LCD screens with logins scribbIed upon them. SpidéringSavvy hackers have realised that many corporate security passwords are made up of words that are connected to the business itself.
Learning corporate literature, website sales materials and even the sites of competition and outlined customers can supply the ammunition to build a custom made word checklist to make use of in a incredible force strike.Really savvy criminals have automated the process and allow a spidering software, similar to those employed by leading search motors to determine keywords, gather and collate the lists for them.Read through NEXT: 10. GuessThe password crackers best friend, of training course, can be the predictability of the consumer. Unless a truly random password has become created making use of software dedicated to the job, a user-generated ‘random' security password is unlikely to become anything of the sort.Instead, thanks to our minds' emotional connection to stuff we including, the possibilities are those arbitrary passwords are based upon our passions, hobbies, animals, family and so on. In truth, passwords have a tendency to be structured on all the things we like to chat about on sociable systems and also consist of in our users.
Password crackers are very likely to appear at this information and create a several - often right - educated guesses when attempting to crack a consumer-level security password without resorting to dictionary or brute drive attacks.